By Tiffany Griffin, Product Manager, Security & Compliance Services
Enforcement is now in effect. On November 10, 2025, the Department of War (DoW) began enforcing Cybersecurity Maturity Model Certification (CMMC) 2.0 requirements across new contracts. This enforcement is backed by the final rule published in Title 48 of the Code of Federal Regulations (CFR), officially amending the Defense Federal Acquisition Regulation Supplement (DFARS) with clauses 252.204-7021 and 252.204-7025.
For defense contractors, cybersecurity is no longer just good hygiene and best practice. It is non-negotiable for doing business with the DoW. Whether you’re self-assessing or relying on third-party validation, compliance is now written into every contract, and it reaches every corner of your supply chain. Prime or sub, there’s no hiding from it: eligibility starts with proof, not promises.
You invested in ServiceNow to simplify complexity, break down silos, and gain real visibility into your operations, not to drown in manual compliance tasks. Now is the time to let that investment deliver real value. Our team at Securitybricks is here to help you turn ServiceNow into your compliance command center and build a resilient, audit-ready operation that stands out in the DoW supply chain.
This guide delivers a practical CMMC Readiness Checklist, built for defense contractors working inside ServiceNow. You’ll see exactly how to put the ServiceNow CMMC 2.0 Accelerator and Contract Flow-down Accelerator to work so you can take control of your compliance journey and focus on what really moves your business forward.
Understanding the New CFR Ruling
The final rule launched a three-year phased rollout of CMMC requirements. By Year 4, every contractor in the Defense Industrial Base (DIB) must be fully compliant. The rule embeds cybersecurity requirements directly into contracts, making CMMC compliance a condition for award.
Highlights of the New CFR Ruling:
- No grace period: Enforcement begins immediately for new solicitations.
- Three-tiered model: Level 1 (self-assessment), Level 2 (self-assessment or third-party certification), and Level 3 (government-led assessments).
- Mandatory for subcontractors: Flow-down requirements extend compliance obligations across the supply chain.
CMMC Readiness Solutions by Securitybricks
Proper preparation for CMMC 2.0 compliance requires a clear understanding of the tools available to streamline and support your organization’s efforts. Securitybricks offers two key ServiceNow solutions to strengthen your compliance strategy: the CMMC 2.0 Accelerator and the CMMC 2.0 Contract Flow-down Accelerator.
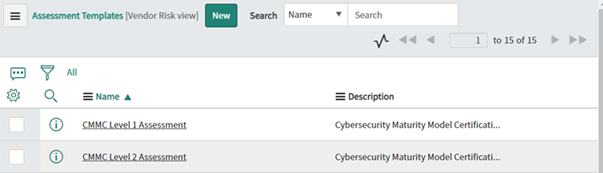
Figure 1: Templates available to self-assess
CMMC 2.0 Accelerator
Built on ServiceNow IRM Pro, the CMMC 2.0 Accelerator serves as an integrated platform for managing all aspects of CMMC readiness and ongoing compliance activities. This solution provides organizations with specialized readiness tools, real-time dashboards, and automated workflows that address both Level 1 and Level 2 certification requirements.
The Accelerator centralizes several key functions, including:
- Control Mapping
- Evidence Collection
- Assessment Tracking
- Remediation Management
By consolidating these processes, organizations can more easily achieve and maintain compliance throughout their enterprise.
CMMC 2.0 Contract Flow-down Accelerator
The Contract Flow-down Accelerator complements the CMMC 2.0 Accelerator by targeting the essential need for subcontractor compliance within the supply chain.
This tool automates the identification and assignment of CMMC flow-down requirements to subcontractors, ensuring obligations are communicated and monitored effectively. By tracking compliance responsibilities across all parties, the solution helps minimize supply chain vulnerabilities and supports comprehensive enforcement of CMMC standards throughout an organization’s network.
The CMMC Readiness Checklist
Whether your organization is seeking Level 1 or Level 2 certification, the checklist below will help you assess your preparedness and take practical steps toward compliance. The ServiceNow CMMC 2.0 Accelerator simplifies this journey by integrating key readiness tools, dashboards, and workflows into a single scalable platform, supporting compliance efforts across your enterprise. Let’s review the CMMC Readiness Checklist and discover how you can begin preparing for CMMC 2.0 compliance today on the ServiceNow platform.
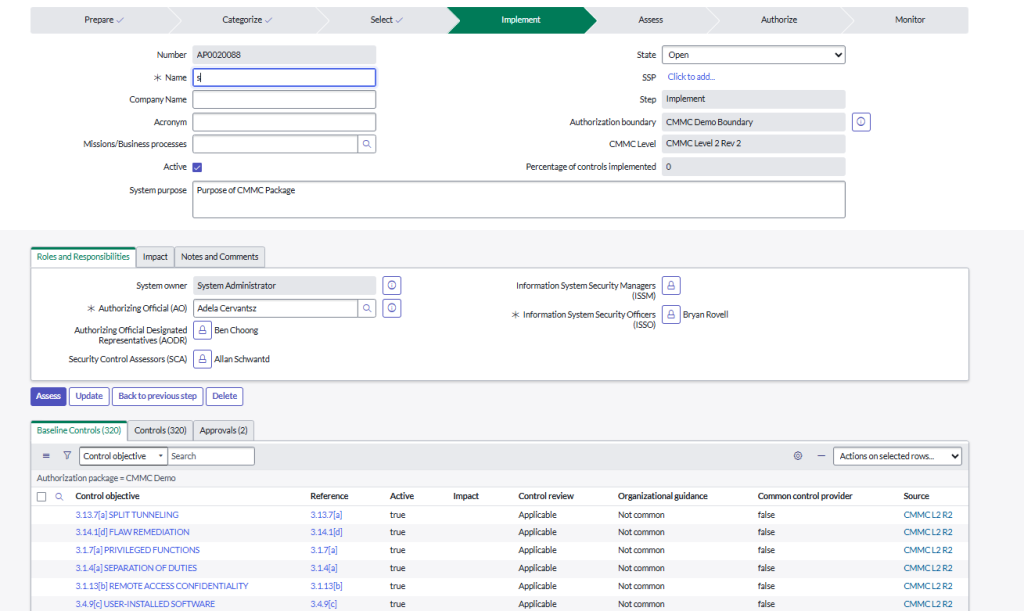
Figure 2: CMMC Control Objectives (User Interface)
1. Scope Your Environment
- Identify systems handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
- Define your CMMC boundary using ServiceNow’s built-in boundary creation tools. Attach network, data flow, and enterprise architecture diagrams to support your boundary definition.
2. Conduct a Gap Analysis
- Map your current controls to NIST SP 800-171 Rev 2.
- Use the CMMC 2.0 Accelerator’s preloaded control objectives to identify deficiencies. Prioritize remediation based on risk and compliance impact.
3. Implement Required Controls
- Configure and assign controls using the Accelerator’s automated workflows. Transition controls from Draft to Attest state to initiate assessments.
- Ensure controls are reviewed and monitored continuously.
4. Centralize Compliance Evidence
- Automate evidence collection to reduce manual effort and errors. Track control status and history in real time using the centralized dashboard.
5. Manage POA&Ms and SSPs
- Generate Plans of Action and Milestones (POA&Ms) for non-compliant controls. Assign issues to stakeholders and track resolution through a five-state workflow.
- Create and attach System Security Plans (SSPs) directly within the Authorization Package.
How the Accelerator Works
Overview of the CMMC Authorization Package
The CMMC Authorization Package is the core component of the Accelerator, providing a robust framework for managing compliance across your organization. This package consolidates all relevant controls and assets within the designated CMMC boundary and guides users through a comprehensive, seven-step workflow that is fully integrated with ServiceNow IRM Pro. By leveraging this approach, organizations can manage their compliance requirements efficiently and systematically.
Seven-Step Workflow for Compliance Management
- Prepare: Start by defining the CMMC boundary within IRM Pro, mapping out all systems, applications, and users that are in scope for compliance. Assets containing CUI are tagged using metadata fields or classification labels, which helps maintain traceability and ensures accurate scoping throughout the compliance process.
- Categorize: Select the appropriate CMMC level for your organization and match corresponding control objectives to existing processes. Using IRM Pro’s asset inventory, CUI-tagged assets are automatically linked to the relevant controls. This step ensures that the compliance boundary remains aligned and that all necessary areas are covered.
- Request Approval: The Authorizing Official (AO) reviews the authorization package to verify that all assets containing CUI are properly tagged and that the boundary mapping is complete. System-generated validation reports assist in confirming asset coverage and control assignments before the process moves forward.
- Select: Appropriate control objectives are brought into the authorization package based on asset classification and the selected CMMC level. IRM Pro’s mapping ensures that only the controls relevant to the defined boundary and CUI data flows are included.
- Implement: Technical and procedural controls are configured, and ownership is assigned to responsible parties. Automated evidence collection scripts can be deployed to collect system logs, configuration baselines, and user activity records directly from endpoints and cloud services. These scripts are designed to reduce manual effort, enforce consistency, and provide timestamped documentation linked to each control.
- Assess: Complete technical questionnaires and evaluate the responses. If any control fails assessment or lacks sufficient supporting evidence, the system automatically generates a noncompliance ticket (or issue record) in the POA&M module. These tickets are routed to stakeholders and tracked through a five-state workflow (i.e., Open, In Progress, Remediation, Review, Closed), supporting remediation tracking and audit traceability.
- Authorize & Monitor: Finalize compliance status based on AO approval and evidence review. Continuous monitoring is enabled by scheduling recurring automated evidence scripts and dashboard alerts for control drift or changes in CUI assets. The SSP is dynamically generated, detailing technical architecture, asset inventory (including CUI tagging), implemented controls, boundary diagrams, and system interconnections. SSPs are version-controlled and attached within the Authorization Package to support real-time updates and audit readiness.
Lifecycle Management of Controls
- Each control advances through clearly defined lifecycle states: Draft, Attest, Review, Monitor, and Retired. Transitions between these states are triggered by evidence uploads, results from automated scripts, or the resolution of noncompliance tickets.
- This structured approach ensures rigorous compliance and traceability of all CUI assets and controls throughout their lifecycle.
Real-Time Monitoring and Reporting
The Accelerator’s dashboard provides:
- Live compliance metrics
- Assessment status tracking
- Automated attestation triggers
- Historical data for audit readiness
This transparency empowers stakeholders to make informed decisions and maintain compliance over time.
Who Should Use the Accelerator?
The ServiceNow application is designed for:
- Compliance Managers/CAM Administrators
- System Owners
- Authorizing Officials (AO)
- Security Control Assessors (SCA)
Each role has tailored access and responsibilities, ensuring accountability and efficiency throughout the compliance lifecycle.
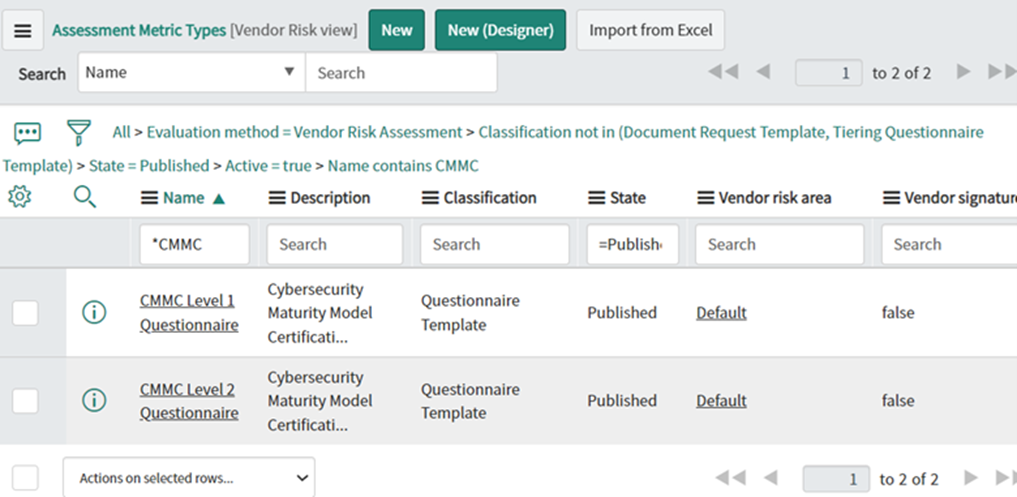
Figure 3: Pre-built CMMC Template and Questionnaire
Ready to Get Started?
Download the ServiceNow CMMC 2.0 Accelerator and take the first step toward automated and audit-ready compliance. Visit securitybricks.io to learn more or contact us to schedule a demo today.